Mapa pojęć
Almost every day we learn from various media about more cases of attacks by cybercriminals. Are you afraid of computer crime? Or have you already become a victim of cybercriminals? Have you heard about their methods of operation? Do you know how to protect yourself from them? One thing is certain, you need to learn as much as possible about the subject to avoid falling victim to cybercrime.
Z różnych mediów niemal codziennie dowiadujemy się o kolejnych przypadkach ataków cyberprzestępców. Czy obawiasz się przestępczości komputerowej? A może już kiedyś padłeś/padłaś ofiarą cyberprzestępców? Słyszałeś/Słyszałaś o ich metodach działania? Wiesz, jak się przed nimi chronić? Jedno jest pewne: trzeba dowiadywać się jak najwięcej na ten temat, żeby nie zostać ich ofiarą.

Study the words or expressions connected with cybercrimes. Then put them in the correct places.
Put the following phrases in the correct places marked with [...]:
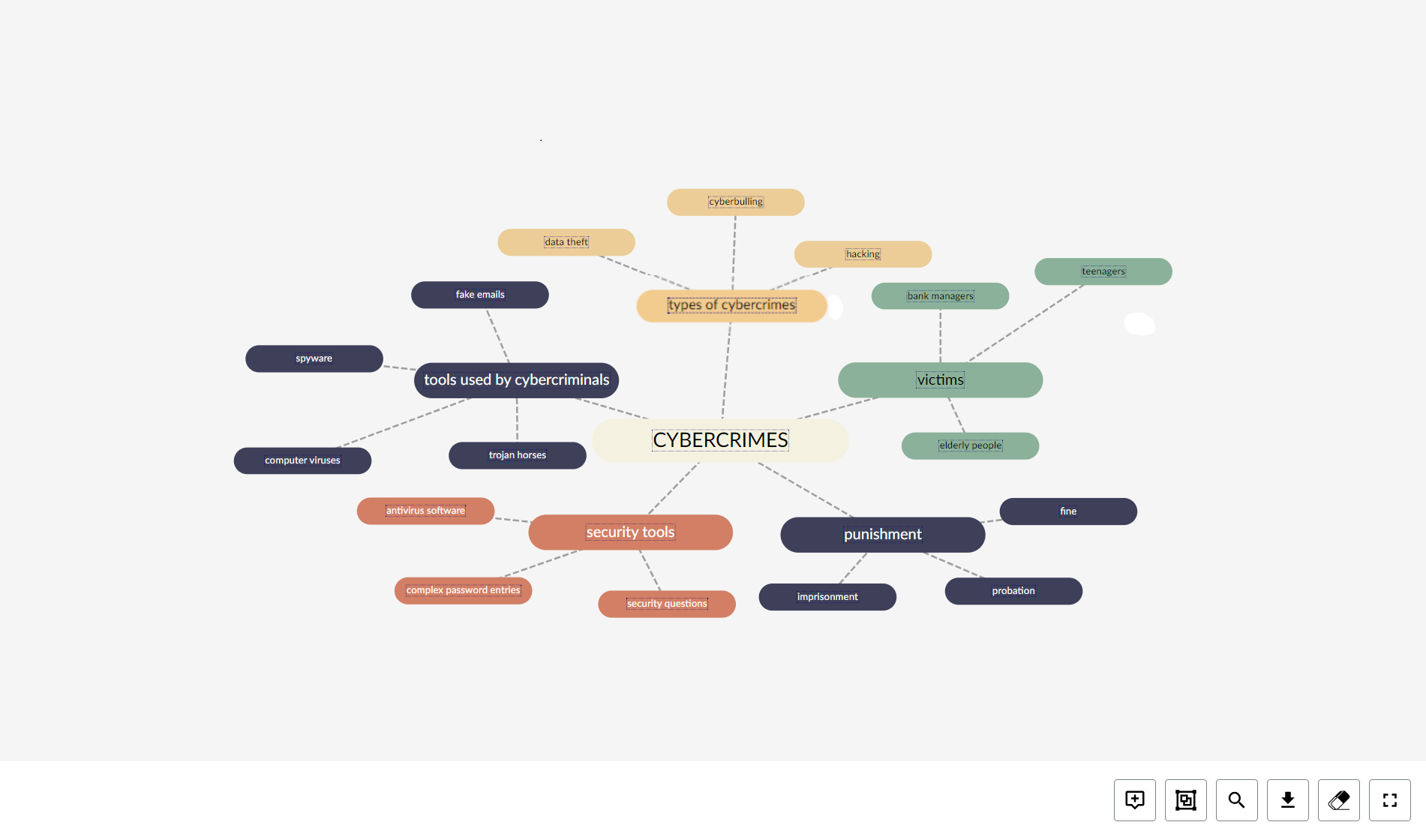
- fake emails
- types of cybercrimes;
- hacking;
- bank managers;
- victims;
- punishment;
- imprisonment
- security questions;
- security tools;
- tools used by cybercriminals;
Study the dialogue. Then drag the following words or expressions into the correct places in the text.
Drag the words to the correct gaps to complete the dialogue. Then play the recording and check your answers.
Lisa: Hi, Jake! Nice to see you too.
Jake: I must say I need your advice. I don’t know how to help Chris, my best friend.
Lisa: What’s happened?
Jake: He is one of the 1. teenagers, 2. spyware, 3. fake emails, 4. prove, 5. victim who has become a 1. teenagers, 2. spyware, 3. fake emails, 4. prove, 5. victim of cybercriminals arrested last night. Haven’t you heard about it?
Lisa: Oh God, I haven’t. How does he feel now?
Jake: I’m afraid not really well. The criminals sent him some 1. teenagers, 2. spyware, 3. fake emails, 4. prove, 5. victim and this way got control over his computer. That is why the police have even accused him of drug trafficking. Luckily, he is able to 1. teenagers, 2. spyware, 3. fake emails, 4. prove, 5. victim that he doesn’t even know any drug dealers.
Lisa: How terrible.
Jake: Now Chris is looking for a good IT worker who will help get rid of the 1. teenagers, 2. spyware, 3. fake emails, 4. prove, 5. victim that the criminals installed and that controls his computer.
Lisa: Tell Chris I’ll visit him tomorrow. It was nice to see you Jake!
Jake: See you next time.
Get familiar with the following piece of radio news about some cybercrime and complete each gap with one word.
Get familiar with the following piece of radio news about some cybercrime and complete the gaps with the words/expressions.
![Grafika przedstawia rysunkową instrukcję do mapy pojęć. Po lewej stronie pośrodku znajduje się jedenaście ikon, w pięciu kolumnach, do których prowadzą czarne strzałki od przypisanych do nich opisów. W pierwszej kolumnie od lewej u góry widoczna jest ikona dymka z plusem w środku z podpisem: dodawanie kolejnego pola. Poniżej widoczna jest ikona hiperłącza internetowego z podpisem: konwertowanie w link. W kolumnie na prawo od góry widoczna jest ikona skośnej przerywanej szarej linii z podpisem: łączenie lub rozłączanie kafelków kliknij przycisk dla danego pola, a następnie pole, które chcesz połączyć lub rozłączyć. Poniżej znajdują się dwie ikony (jedna ze skośną zieloną, a druga czerwoną linią) z podpisem: zmiana koloru linii, łączącej pola kliknij przycisk dla danego pola, a następnie drugie pole, połączone z pierwszym. W trzeciej kolumnie widoczna jest od góry ikona z literką A, po której prawej stronie widoczna jest strzałka w górę, z podpisem: zwiększanie pól oraz tekstu. Poniżej widoczna jest ikona z literką A, po której prawej stronie widoczna jest strzałka w dół, z podpisem: zmniejszanie pól oraz tekstu. W czwartej kolumnie od góry widoczna jest ikona z dwoma strzałkami biegnącymi po łuku w przeciwnych kierunkach z podpisem: zmiana koloru pola. Poniżej widoczna jest ikona z koszem na śmieci z podpisem: usunięcie danego pola. W piątek kolumnie od góry widoczna jest ikona z szarym kwadratem z małym plusikiem z podpisem: dodawanie załączników, a poniżej ikona z liniami tekstu z podpisem: dodawanie opisu pola. Natomiast po prawej stronie znajduje się sześć ikon w rzędzie kolumnach, do których prowadzą czarne strzałki od przypisanych do nich opisów. Od lewej widoczna jest ikona dymka z plusem w środku z podpisem: dodawanie kolejnego pola; ikona z kwadratem, w który wpisane są dwa nakładające się kwadraty z podpisem: grupowanie elementów zaznacz dany obszar lewym przyciskiem myszy, a następnie nadaj mu nazwę klikając ołówek i wpisując tekst w pojawiające się białe okno; ikona z lupą z podpisem: ustawianie domyślnego widoku; ikona ze strzałką w dół, poniżej której pozioma kreska z podpisem: pobieranie i drukowanie mapy pojęć; ikona z gumką z podpisem: wyczyść mapę i ikona trybu pełnoekranowego z podpisem: tryb pełnoekranowy. Po prawej stronie u dołu widoczne jest również biały prostokąt z napisem [wpisz tekst], który nachodzi na pole z dwoma żółtymi elementami z napisem Element 1 i Element 2. Poniżej podpis: aby usunąć grupowanie, kliknij przycisk „Rozgrupuj”.](https://static.zpe.gov.pl/portal/f/res-minimized/RADYhvE2l8OB1/1712568372/2dLm2A26F6NqMeJwN1ZiCNTUxEnjwcXj.png)